Cybercriminal Accused Of Multi-Million Dollar Office365 Executive Account Breach
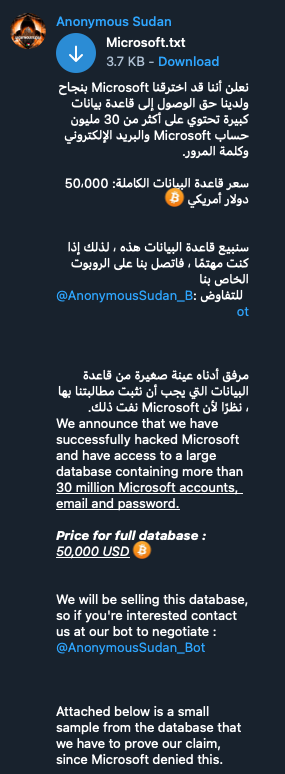
Table of Contents
The Mechanics of the Office365 Executive Account Compromise
The alleged breach highlights the sophisticated techniques employed by modern cybercriminals. Understanding these methods is crucial for effective prevention.
Phishing and Social Engineering
The most likely entry point for this alleged Office365 executive account breach was through phishing and social engineering tactics. Cybercriminals often target high-level executives with spear phishing campaigns, crafting highly personalized emails designed to appear legitimate. These emails may mimic communications from trusted sources, such as board members, clients, or even the CEO themselves.
- Spear phishing: Highly targeted emails designed to trick specific individuals into revealing sensitive information.
- CEO fraud (or Business Email Compromise - BEC): Emails that impersonate executives to initiate fraudulent wire transfers or other financial transactions.
- Pretexting: Creating a false sense of urgency or authority to manipulate victims into taking action.
For example, an email might appear to be from a financial institution, urging immediate action on a supposedly urgent transaction. Successful social engineering exploits human psychology, leveraging trust and urgency to bypass security protocols.
Exploiting Weaknesses in Multi-Factor Authentication (MFA)
While multi-factor authentication (MFA) is a crucial security layer, it's not foolproof. This alleged Office365 executive account breach may have exploited vulnerabilities in the implementation or user practices related to MFA.
- Weak MFA methods: Using easily guessable codes or readily available authentication apps.
- Compromised devices: If an executive's phone or computer used for MFA is compromised, the attacker gains access.
- Phishing attacks bypassing MFA: Sophisticated attacks can sometimes circumvent MFA by obtaining access to the user's recovery codes or phone number.
Strong password policies and robust MFA enforcement are critical for mitigating this risk. Organizations should choose MFA methods that offer the highest level of security and regularly audit their MFA implementations.
Post-Breach Activities
Once access was gained, the cybercriminal likely engaged in various activities to maximize their gain and minimize detection.
- Data exfiltration: Stealing sensitive data, including financial records, customer information, and intellectual property.
- Wire fraud: Initiating fraudulent wire transfers to offshore accounts.
- Account takeover: Maintaining access to the compromised accounts for extended periods to conduct further illicit activities.
- Data wiping and obfuscation: Attempting to delete logs and cover their tracks.
These post-breach activities highlight the importance of robust monitoring and incident response plans.
The Financial and Reputational Damage of the Office365 Breach
The alleged Office365 executive account breach resulted in significant financial and reputational damage.
Direct Financial Losses
The direct financial loss in this alleged breach reportedly amounts to several million dollars, representing a substantial blow to the victimized company.
- Stolen funds: Millions of dollars transferred to offshore accounts.
- Forensic investigations: The costs associated with hiring cybersecurity experts to investigate the breach.
- Legal fees: Expenses related to legal representation and potential lawsuits.
- Regulatory fines: Penalties imposed by regulatory bodies for non-compliance with data protection regulations.
These costs extend far beyond the initial theft.
Reputational Harm
The reputational damage is equally significant, potentially impacting long-term profitability and investor confidence.
- Loss of investor confidence: Negative publicity can lead to a decline in stock prices and difficulty securing future investments.
- Damage to brand trust: Customers may lose faith in the company's ability to protect their data and information.
- Negative media coverage: News reports of the breach can severely damage the company's image.
- Loss of customer relationships: Customers may choose to do business with competitors perceived as more secure.
Preventing Future Office365 Executive Account Breaches: Best Practices and Mitigation Strategies
Preventing future Office365 executive account breaches requires a multi-layered approach encompassing technological safeguards and employee training.
Strengthening Password Security
Strong password policies are fundamental.
- Password managers: Use robust password management tools to generate and securely store complex passwords.
- Regular password changes: Enforce regular password changes to mitigate the risk of compromised credentials.
- Password complexity requirements: Implement strict rules for password length, character types, and complexity.
Implementing Robust Multi-Factor Authentication (MFA)
MFA is not optional; it's essential.
- Multiple MFA methods: Employ a combination of methods like OTP (one-time passwords), biometrics, and hardware security keys.
- Regular MFA security audits: Conduct routine audits to assess the effectiveness and identify vulnerabilities in your MFA implementation.
- Conditional access policies: Implement policies that restrict access based on location, device, and other factors.
Security Awareness Training
Investing in comprehensive security awareness training is critical.
- Regular training programs: Conduct regular training sessions to educate employees on identifying and avoiding phishing attempts.
- Simulated phishing campaigns: Use simulated phishing campaigns to assess employee vulnerability and reinforce training effectiveness.
- Reporting mechanisms: Establish clear channels for employees to report suspicious emails and activities.
Regular Security Audits and Penetration Testing
Proactive security measures are paramount.
- Regular security assessments: Conduct periodic vulnerability assessments to identify and remediate weaknesses in your systems.
- Penetration testing: Employ penetration testing to simulate real-world attacks and expose potential vulnerabilities.
Conclusion: Protecting Your Business from Office365 Executive Account Breaches
The alleged multi-million dollar Office365 executive account breach serves as a stark reminder of the ever-present threat of cyberattacks. The financial and reputational consequences can be catastrophic. Robust security measures, including strong passwords, robust MFA implementation, comprehensive security awareness training, and regular security audits, are not optional – they are essential for protecting your organization from similar Office365 executive account breaches. Investing in these measures is an investment in the future security and stability of your business. For more information on strengthening your cybersecurity posture, explore resources from [insert reputable cybersecurity organizations or websites here]. Don't wait for an Office365 executive account breach to happen – take action today to protect your business.

Featured Posts
-
 The Closure Of Ryujinx Emulator Details Emerge
Apr 24, 2025
The Closure Of Ryujinx Emulator Details Emerge
Apr 24, 2025 -
 Saudi India Oil Refinery Partnership A Major Development
Apr 24, 2025
Saudi India Oil Refinery Partnership A Major Development
Apr 24, 2025 -
 John Travoltas Miami Steakhouse Adventure A Pulp Fiction Inspired Meal
Apr 24, 2025
John Travoltas Miami Steakhouse Adventure A Pulp Fiction Inspired Meal
Apr 24, 2025 -
 Dollar Advances Trumps Cooling Rhetoric Boosts Usd Value
Apr 24, 2025
Dollar Advances Trumps Cooling Rhetoric Boosts Usd Value
Apr 24, 2025 -
 Is Betting On Natural Disasters The New Normal The Case Of The La Fires
Apr 24, 2025
Is Betting On Natural Disasters The New Normal The Case Of The La Fires
Apr 24, 2025
