Cybercriminal Makes Millions From Executive Office365 Infiltration
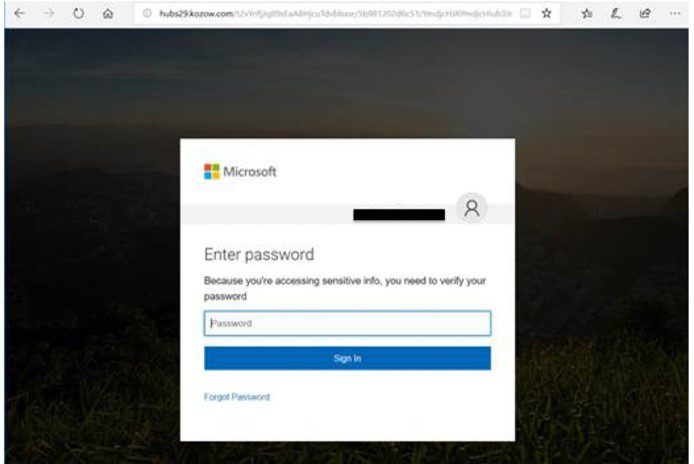
Table of Contents
A recent study revealed a staggering 40% increase in Office 365 breaches targeting executive-level accounts in the past year. This alarming statistic highlights the growing threat of Executive Office365 Infiltration, a sophisticated form of cybercrime that can cripple businesses and cost millions. One notorious cybercriminal recently amassed a fortune by exploiting vulnerabilities in executive Office 365 accounts, showcasing the devastating potential of this type of attack. This article will explore the methods used in these attacks, the devastating consequences they can bring, and crucially, the steps you can take to prevent Executive Office365 Infiltration within your own organization.
H2: Methods Employed by Cybercriminals in Executive Office365 Infiltration:
Cybercriminals employ increasingly sophisticated tactics to infiltrate executive Office 365 accounts. Their methods are designed to bypass traditional security measures and exploit human vulnerabilities.
H3: Phishing and Spear Phishing Attacks:
- Sophisticated Phishing Emails: Cybercriminals craft highly convincing phishing emails tailored to the specific interests and roles of executives. These emails often mimic legitimate communications from trusted sources, creating a sense of urgency and trust.
- Impersonation and Social Engineering: Attackers often impersonate colleagues, clients, or even senior management to trick executives into revealing sensitive information or clicking malicious links. They use social engineering techniques to manipulate their victims.
- Convincing Lures and Attachments: Phishing emails might contain enticing offers, urgent requests for information, or seemingly innocuous attachments containing malware. These attachments might appear as invoices, contracts, or company reports.
- Spear Phishing Effectiveness: Spear phishing is particularly effective against high-value targets like executives because it leverages personalized information to increase the chances of success.
H3: Exploiting Weak Passwords and Credential Stuffing:
- Weak Passwords: Many executives still use weak, easily guessable passwords, making them prime targets for cybercriminals. Simple passwords or passwords reused across multiple accounts are especially vulnerable.
- Credential Stuffing: Cybercriminals use stolen credentials from other data breaches to attempt to access Office 365 accounts. This technique, known as credential stuffing, becomes extremely effective when executives reuse the same password across multiple platforms.
- Preventative Measures: Utilizing strong, unique passwords for each account, along with password managers and multi-factor authentication (MFA), are crucial preventative measures.
H3: Malware and Ransomware Infections:
- Malware for Access: Malware can be used to gain initial access to a system and then used to compromise Office 365 accounts. This could be through malicious attachments or compromised websites.
- Ransomware Attacks: Ransomware encrypts data, rendering it inaccessible unless a ransom is paid. This can disrupt operations and cause significant financial losses. Data exfiltration often happens before encryption.
- Third-Party Applications: Compromised third-party applications integrated with Office 365 can provide a backdoor for attackers. Thorough vetting of all third-party apps is essential.
H2: Devastating Consequences of Executive Office365 Infiltration:
The consequences of successful Executive Office365 Infiltration can be far-reaching and devastating.
H3: Financial Losses:
- Direct Financial Losses: Direct financial losses include stolen funds, ransom payments, legal fees associated with data breaches, and the costs of recovery and remediation.
- Reputational Damage and Investor Loss: Damage to reputation can lead to loss of investor confidence and decreased market value.
H3: Data Breaches and Reputational Damage:
- Sensitive Data Exposure: Breaches expose sensitive company data, intellectual property, customer information, and confidential business strategies.
- Regulatory Fines and Legal Actions: Organizations face potential regulatory fines and lawsuits following data breaches.
- Impact on Customer Trust: Damage to reputation can significantly impact customer trust and lead to a loss of business.
H3: Operational Disruptions:
- Ransomware-Induced Disruptions: Ransomware attacks can severely disrupt business operations, halting productivity and causing significant financial losses.
- Recovery and Remediation: Recovering from a security breach requires significant time, resources, and expertise.
- Long-Term Productivity Impacts: The aftermath of an attack can negatively impact productivity and efficiency for extended periods.
H2: Protecting Your Organization from Executive Office365 Infiltration:
Protecting your organization from Executive Office365 Infiltration requires a multi-layered approach.
H3: Implementing Robust Security Measures:
- Multi-Factor Authentication (MFA): Implement MFA for all accounts to add an extra layer of security.
- Security Awareness Training: Conduct regular security awareness training for all employees, focusing on phishing and social engineering techniques.
- Strong Password Policies: Enforce strong password policies and encourage the use of password management tools.
- Regular Security Audits and Penetration Testing: Perform regular security audits and penetration testing to identify vulnerabilities.
H3: Utilizing Advanced Threat Protection:
- Advanced Threat Protection Tools: Employ advanced threat protection tools to detect and block malicious emails and attachments.
- Email Security Solutions: Utilize email security solutions with sandboxing capabilities to analyze suspicious attachments in a safe environment.
- Data Loss Prevention (DLP): Implement DLP tools to prevent sensitive data from leaving the network.
H3: Incident Response Planning:
- Comprehensive Incident Response Plan: Develop a comprehensive incident response plan that outlines procedures to follow in the event of a security breach.
- Regular Plan Testing: Regularly test the incident response plan to ensure its effectiveness and identify areas for improvement.
- Containment and Mitigation: Know how to quickly contain and mitigate the impact of a security breach to minimize damage.
3. Conclusion: Preventing Executive Office365 Infiltration – A Call to Action
This article has highlighted the sophisticated methods used in Executive Office365 Infiltration, the devastating consequences for businesses, and the crucial steps needed to prevent these attacks. Ignoring the threat of Executive Office365 infiltration leaves your organization vulnerable to significant financial losses, reputational damage, and operational disruptions. Proactive measures, including robust security measures, advanced threat protection, and a comprehensive incident response plan, are essential for protecting your organization. Don't wait for a breach to occur. Invest in comprehensive Office 365 security solutions and consult with cybersecurity experts to assess your vulnerabilities and implement effective preventative measures. Protecting your executive accounts and preventing Executive Office365 infiltration is not just a good idea – it's a necessity for business survival in today's digital landscape.

Featured Posts
-
 Brace For Impact Stock Market Challenges And Investor Response
Apr 22, 2025
Brace For Impact Stock Market Challenges And Investor Response
Apr 22, 2025 -
 Pope Francis Legacy The Conclaves Crucial Test
Apr 22, 2025
Pope Francis Legacy The Conclaves Crucial Test
Apr 22, 2025 -
 Trump Protests 2024 A Look At Demonstrations Across America
Apr 22, 2025
Trump Protests 2024 A Look At Demonstrations Across America
Apr 22, 2025 -
 Trumps Trade Legacy A Reassessment Of Americas Financial Standing
Apr 22, 2025
Trumps Trade Legacy A Reassessment Of Americas Financial Standing
Apr 22, 2025 -
 Blue Origins New Shepard Launch Delayed Subsystem Issue Cited
Apr 22, 2025
Blue Origins New Shepard Launch Delayed Subsystem Issue Cited
Apr 22, 2025
