Office365 Data Breach: Millions Stolen, Hacker Indicted
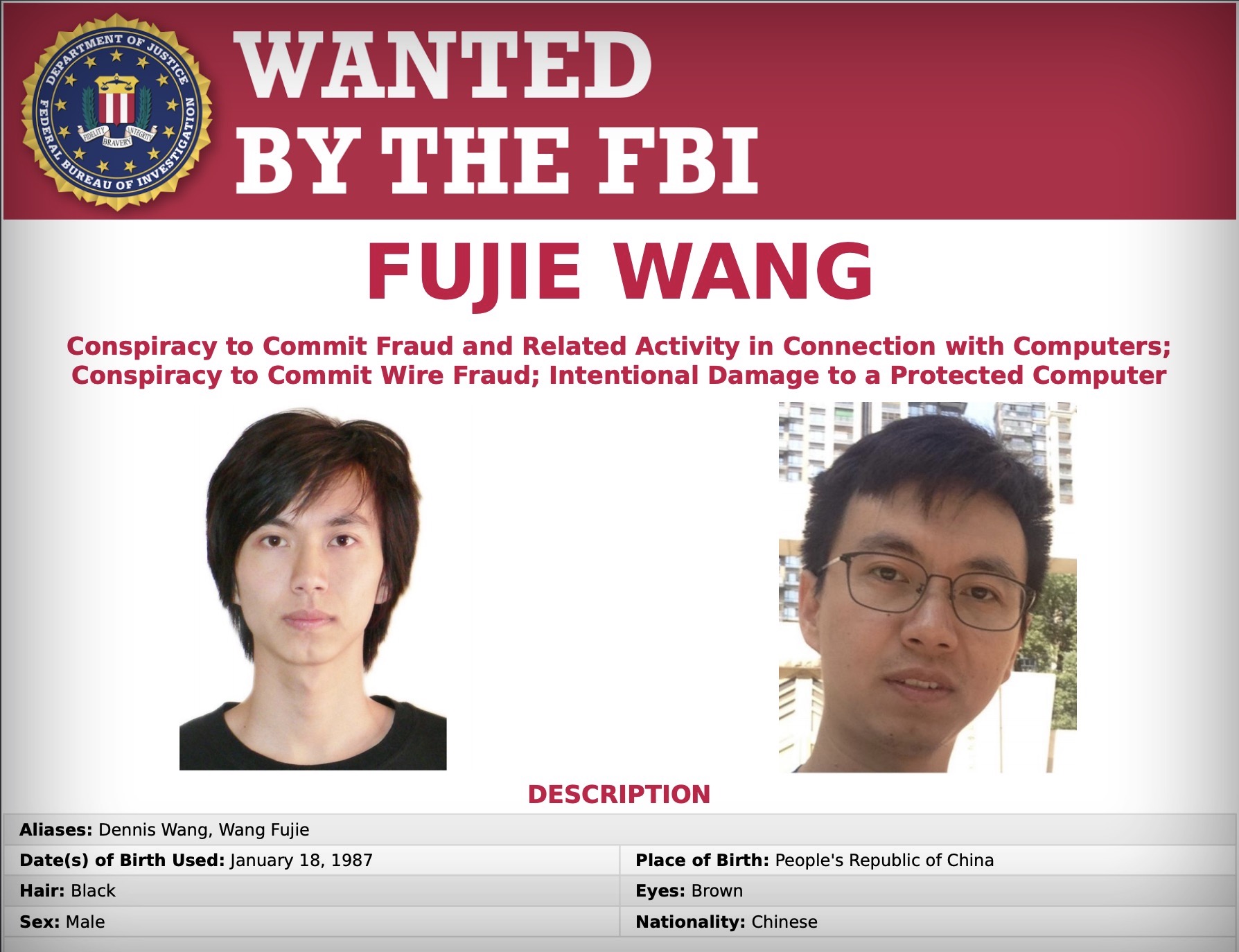
Table of Contents
The Scale and Scope of the Office365 Data Breach
The sheer magnitude of this Office365 security breach is staggering. Millions of users across numerous geographical regions were affected, suffering a significant compromise of their sensitive data. The breach wasn't limited to a single region; reports indicate widespread impact across North America, Europe, and Asia. The types of data stolen were alarmingly comprehensive:
- Emails: Including both personal and business communications, often containing sensitive personal information and confidential business strategies.
- Documents: Compromised documents ranged from financial reports and legal agreements to personal medical records and intellectual property.
- Sensitive Personal Information: Data like addresses, phone numbers, and social security numbers were readily accessible to the hacker.
- Financial Data: In some cases, access to banking details and credit card information was obtained, leading to significant financial risks for the victims.
This Microsoft data breach highlights the devastating consequences of successful cyberattacks, emphasizing the need for robust Office 365 security measures and proactive cybersecurity strategies. The scale of data theft underscores the urgent need for improved data protection practices across all levels.
How the Hacker Gained Access: Exploiting Vulnerabilities in Office365
The hacker employed sophisticated techniques to breach the Office365 platform. Initial investigations suggest a multi-pronged approach combining several methods:
- Phishing Attacks: Highly targeted phishing emails were sent to employees, tricking them into revealing their login credentials. These emails often mimicked legitimate communications from within the organization or trusted external sources.
- Malware Infection: Once initial access was gained, malware was deployed to spread laterally across the network, gaining access to an increasingly larger pool of data.
- Exploiting Zero-Day Vulnerabilities: The hacker may have exploited previously unknown security flaws (zero-day vulnerabilities) within the Office365 platform itself. This highlights the ever-evolving nature of cyber threats and the need for constant vigilance.
The hacker's techniques demonstrated a high level of skill and knowledge of the Office365 system, emphasizing the need for ongoing security updates and robust security protocols. Bypassing security measures required a meticulous approach, leveraging weaknesses in both human behavior and technological infrastructure.
The Impact of the Office365 Data Breach: Financial and Reputational Losses
The consequences of this Office365 data breach are far-reaching and devastating. For individuals, the impact includes:
- Identity theft: Stolen personal information can be used for identity theft, leading to significant financial and emotional distress.
- Financial losses: Compromised financial data can result in fraudulent transactions and financial losses.
- Emotional distress: The violation of privacy and the uncertainty surrounding potential future consequences can cause significant emotional distress.
For organizations, the fallout is even more severe, encompassing:
- Reputational damage: A data breach can severely damage an organization's reputation, leading to loss of customer trust and business opportunities.
- Legal liabilities: Organizations face legal ramifications, including potential lawsuits and regulatory fines, stemming from their failure to adequately protect customer data.
- Financial losses: The costs associated with investigations, legal fees, remediation efforts, and potential compensation to victims can be substantial.
The regulatory compliance burden following such a breach is immense, potentially leading to significant financial penalties and long-term reputational damage.
The Hacker's Indictment and Legal Proceedings
The indictment of the hacker represents a significant step in holding cybercriminals accountable for their actions. The charges brought against the individual include various counts related to:
- Unauthorized access to computer systems: The core charge relates to the illegal access and use of the Office365 systems.
- Data theft: The indictment covers the theft of millions of sensitive data records.
- Identity theft: The charges may also include counts related to identity theft based on the stolen personal information.
The legal process, including evidence presented during the indictment, highlights the seriousness of cybercrime and the need for stronger cyber security laws and enforcement. The potential penalties, which could include substantial prison time and hefty fines, serve as a deterrent to future cyberattacks. This prosecution is crucial for setting precedents in cybercrime and demonstrates a commitment to tackling the growing problem of data breaches.
Protecting Yourself from Future Office365 Data Breaches
Protecting yourself from future Office365 data breaches requires a multi-layered approach:
- Strong Password Management: Use unique, complex passwords for all your accounts, including Office365. Consider using a password manager to help you generate and manage strong passwords securely.
- Multi-Factor Authentication (MFA): Enable MFA for your Office365 account. This adds an extra layer of security by requiring a second verification method, such as a code sent to your phone, in addition to your password.
- Regular Security Updates: Keep your Office365 software and applications updated with the latest security patches.
- Phishing Prevention: Be vigilant about suspicious emails and links. Never click on links or open attachments from unknown senders. Report suspicious emails to your IT department.
- Cybersecurity Awareness Training: Regular employee training on cybersecurity best practices is crucial for mitigating human error, a common vulnerability exploited in phishing attacks.
These proactive measures, along with a culture of security awareness within organizations, are essential for mitigating the risk of future Office365 data breaches.
Conclusion: Strengthening Office365 Security in the Wake of the Breach
The Office365 data breach serves as a stark reminder of the ever-present threat of cyberattacks and the devastating consequences they can have. The scale of the breach and the significant financial and reputational losses underscore the importance of proactive security measures. By implementing robust security protocols, including strong password management, multi-factor authentication, regular security updates, phishing prevention, and comprehensive cybersecurity awareness training, individuals and organizations can significantly reduce their vulnerability to future Office365 data breaches. Review your Office365 security settings today and take steps to enhance your protection. For further information on Office365 security best practices, consult Microsoft's official security resources. Don't wait until it's too late – protect your data and prevent becoming a victim of a future Office365 data breach.

Featured Posts
-
 Us Dollar Gains Momentum Against Major Peers Amidst Eased Trump Rhetoric
Apr 24, 2025
Us Dollar Gains Momentum Against Major Peers Amidst Eased Trump Rhetoric
Apr 24, 2025 -
 Federal Funding Cuts And The Rising Risk Of Tornadoes
Apr 24, 2025
Federal Funding Cuts And The Rising Risk Of Tornadoes
Apr 24, 2025 -
 Trump Affirms Continued Employment Of Federal Reserve Chair Powell
Apr 24, 2025
Trump Affirms Continued Employment Of Federal Reserve Chair Powell
Apr 24, 2025 -
 Double Trouble In Hollywood The Writers And Actors Joint Strike
Apr 24, 2025
Double Trouble In Hollywood The Writers And Actors Joint Strike
Apr 24, 2025 -
 Judge Abrego Garcia Issues Strict Order Against Stonewalling By Us Lawyers
Apr 24, 2025
Judge Abrego Garcia Issues Strict Order Against Stonewalling By Us Lawyers
Apr 24, 2025
