Federal Investigation: Millions Stolen Via Executive Office365 Compromise

Table of Contents
The Scale of the Breach and the Federal Investigation
The financial losses in this Executive Office 365 compromise are staggering, with estimates exceeding several million dollars. While the exact number of victims remains unclear, the investigation suggests a significant number of organizations may have been affected. The Federal Bureau of Investigation (FBI), in conjunction with the Department of Justice (DOJ), is leading the investigation, though specific details are currently limited due to the ongoing nature of the proceedings. Public statements have been cautious, emphasizing the seriousness of the situation and the commitment to bringing those responsible to justice.
- Total financial loss estimated: Millions of dollars
- Number of organizations potentially compromised: Currently under investigation, but likely significant.
- Agencies involved in the investigation: FBI, DOJ, potentially others.
- Timeline of the investigation: Ongoing; expected to last for several months.
Methods Used by Cybercriminals in the Office 365 Compromise
The attackers employed sophisticated techniques to breach Office 365 security. Initial investigations point towards a multi-pronged approach, leveraging common vulnerabilities often exploited in large-scale cybercrime.
- Phishing campaigns targeting employees: Malicious emails mimicking legitimate communications likely tricked employees into revealing login credentials.
- Exploitation of weak passwords or reused credentials: Many breaches stem from easily guessable or recycled passwords, highlighting the need for robust password management.
- Use of malware or malicious links: Compromised attachments or links within emails could have delivered malware that granted access to sensitive data.
- Methods of money laundering and transfer: Investigators are actively tracing the flow of funds to uncover the criminals' money laundering schemes. This often involves complex international transactions.
The Implications for Businesses and Organizations
This Office 365 compromise serves as a stark reminder of the potential consequences of inadequate cybersecurity. The repercussions extend far beyond financial losses.
- Financial losses due to data breaches and theft: The direct cost of stolen funds is substantial, but indirect costs like legal fees and recovery efforts can be equally significant.
- Reputational damage and loss of customer trust: A security breach can severely damage an organization's reputation, leading to customer churn and lost business opportunities.
- Legal penalties and regulatory fines (GDPR, CCPA, etc.): Non-compliance with data privacy regulations can result in hefty fines and legal action.
- Operational disruptions and business downtime: The disruption caused by a security breach can significantly impact operations and productivity.
Best Practices for Protecting Your Office 365 Environment
Protecting your organization from a similar Office 365 compromise requires a proactive and multi-layered approach.
- Implement multi-factor authentication (MFA): MFA adds an extra layer of security, making it significantly harder for attackers to access accounts even if they have stolen passwords.
- Enforce strong password policies and password management: Require complex passwords, enforce regular password changes, and consider using a password manager.
- Regularly update software and security patches: Keeping software up-to-date is crucial for patching known vulnerabilities.
- Conduct regular employee security awareness training: Educate employees about phishing scams, malware, and safe online practices.
- Utilize advanced threat protection features: Office 365 offers various advanced threat protection tools that can detect and prevent malicious activities.
- Implement security information and event management (SIEM): SIEM systems monitor security events and provide alerts for potential threats.
Conclusion: Safeguarding Your Organization from an Office 365 Compromise
The federal investigation into the millions stolen via an Executive Office 365 compromise highlights the critical need for robust cybersecurity measures. The financial losses and reputational damage caused by this breach underscore the importance of proactive security strategies and incident response planning. Strengthen your Office 365 security by implementing the best practices outlined above. Don't wait for a similar Office 365 compromise to affect your organization; take immediate steps to prevent a Federal Investigation. Assess your current security posture today and invest in the tools and training necessary to protect your valuable data and prevent a potentially devastating breach. For further information on enhancing your security, refer to resources like and .

Featured Posts
-
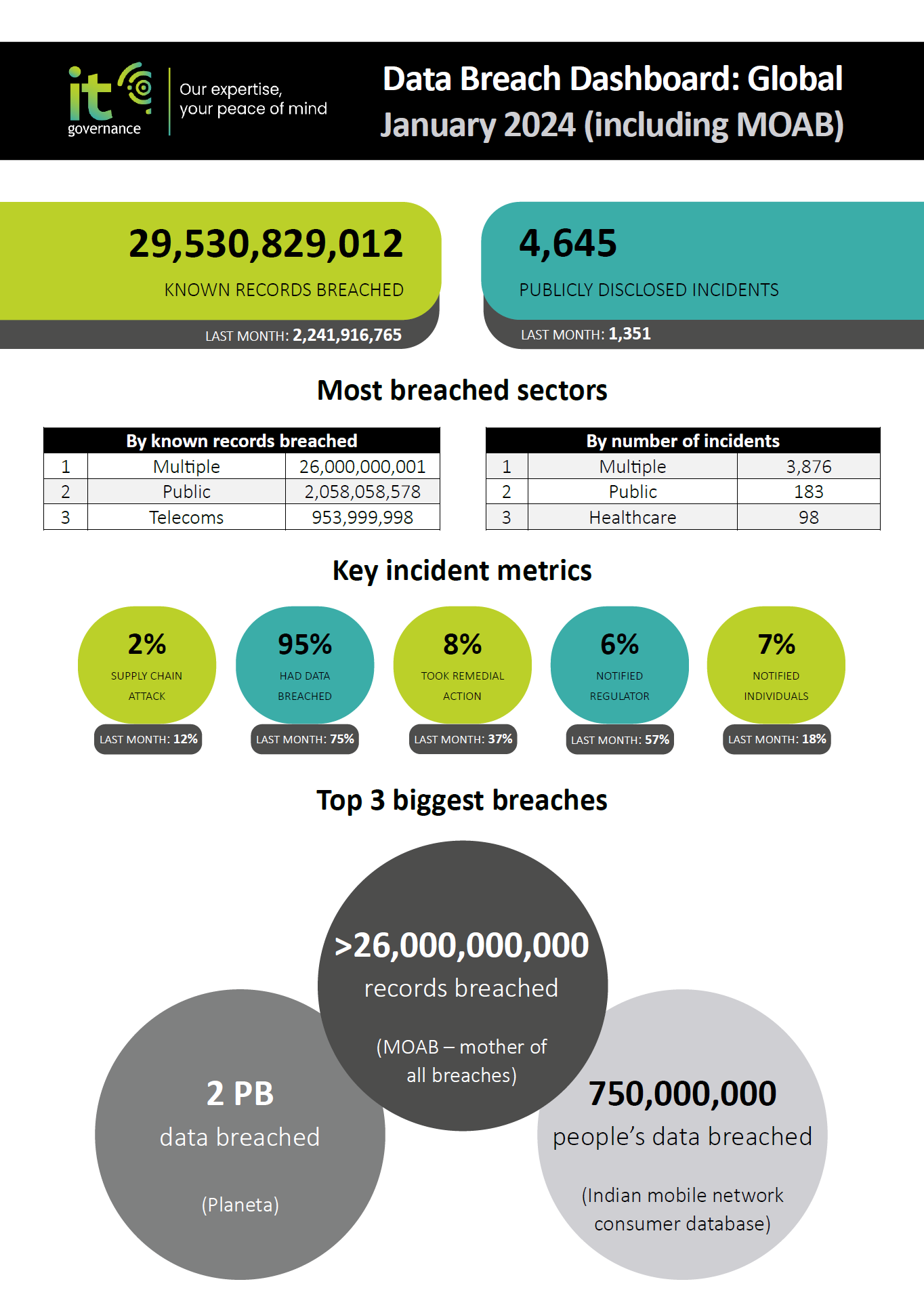 T Mobiles 16 Million Data Breach Fine Three Years Of Security Failures
Apr 22, 2025
T Mobiles 16 Million Data Breach Fine Three Years Of Security Failures
Apr 22, 2025 -
 Pope Francis Legacy Key Issues For The Papal Election
Apr 22, 2025
Pope Francis Legacy Key Issues For The Papal Election
Apr 22, 2025 -
 Mixed Reactions To Fsus Decision To Resume Classes After Deadly Shooting
Apr 22, 2025
Mixed Reactions To Fsus Decision To Resume Classes After Deadly Shooting
Apr 22, 2025 -
 The Impact Of Tariffs On Chinas Export Oriented Economy
Apr 22, 2025
The Impact Of Tariffs On Chinas Export Oriented Economy
Apr 22, 2025 -
 Why Nike Shoe Production Remains A Challenge For Robots
Apr 22, 2025
Why Nike Shoe Production Remains A Challenge For Robots
Apr 22, 2025
