Millions Stolen: Inside The Office365 Executive Inbox Hacking Scheme
Table of Contents
Understanding the Office365 Executive Inbox Hacking Technique
Office365 executive inbox hacking relies on gaining unauthorized access to the email accounts of senior executives. This access is then used to intercept sensitive financial information and execute fraudulent transactions. Hackers employ a variety of methods to achieve this, often combining technical exploits with social engineering tactics.
-
Phishing emails designed to mimic legitimate communications: These emails often appear to come from trusted sources, such as colleagues, clients, or even the CEO themselves. They may contain malicious links or attachments that download malware or request login credentials. Sophisticated phishing campaigns often utilize spear-phishing techniques, tailoring the message to the specific target.
-
Exploiting weak or reused passwords: Many executives reuse passwords across multiple platforms, making it easier for hackers to gain access to their Office365 accounts if one of their other accounts is compromised. Weak passwords, easily guessable or easily cracked, are another significant vulnerability.
-
Utilizing social engineering tactics to manipulate victims: Hackers may use social engineering to trick executives into revealing sensitive information, such as passwords or one-time codes. This can involve building relationships with targets, creating a sense of urgency, or exploiting their trust.
-
Compromising third-party applications with access to Office365: Many applications integrate with Office365, providing access to email and other data. If these third-party applications are compromised, hackers can gain access to the executive's Office365 account indirectly.
-
Advanced persistent threats (APTs) gaining long-term access: In some cases, hackers use advanced techniques to gain persistent access to Office365 accounts, remaining undetected for extended periods. These sophisticated attacks often involve exploiting zero-day vulnerabilities and using custom malware.
The Financial Ramifications of Executive Inbox Compromise
The financial consequences of a successful Office365 executive inbox hacking attack can be devastating. Organizations have reported losing millions of dollars due to these attacks. The impact extends beyond direct financial losses.
-
Wire transfer fraud: Hackers intercept payment instructions, redirecting funds to their own accounts. This is often done by modifying invoices or creating fraudulent payment requests that appear legitimate.
-
Invoice fraud: Hackers alter payment details on legitimate invoices, subtly changing bank account numbers or routing information to redirect payments.
-
Data breaches leading to reputational damage and fines: Compromised executive inboxes often contain sensitive company data. A data breach can lead to significant reputational damage, regulatory fines, and legal costs.
-
Loss of intellectual property: Access to an executive's inbox can provide hackers with access to sensitive intellectual property, such as product designs, strategic plans, and client information.
-
Legal fees associated with investigations and recovery efforts: Responding to an Office365 executive inbox hacking attack involves extensive investigations, forensic analysis, and legal action, resulting in substantial legal fees.
Identifying Red Flags and Recognizing an Attack
Recognizing the signs of an Office365 executive inbox hacking attack is crucial for minimizing the damage. Early detection allows for prompt action, potentially limiting the financial and reputational impact.
-
Unusual login attempts from unfamiliar locations: Monitor login activity for attempts from unexpected geographic locations or devices.
-
Unexpected email changes or account modifications: Pay attention to changes in email settings, such as forwarding rules, aliases, or security settings.
-
Suspicious emails requesting urgent financial transactions: Be wary of emails demanding immediate payment, often with threats or a sense of urgency.
-
Unexplained financial discrepancies: Regularly review financial records for any inconsistencies or unusual transactions.
-
Unusual activity on company systems: Monitor system logs and network traffic for signs of unauthorized access or data exfiltration.
Protecting Against Office365 Executive Inbox Hacking
Protecting against Office365 executive inbox hacking requires a multi-layered approach, combining technical security measures with employee training and awareness.
-
Implement multi-factor authentication (MFA) for all accounts: MFA adds an extra layer of security, requiring more than just a password to access an account.
-
Regularly update passwords and enforce strong password policies: Enforce strong, unique passwords and encourage regular password changes. Consider using a password manager to help manage complex passwords.
-
Conduct regular security awareness training for employees: Educate employees about phishing scams, social engineering tactics, and safe email practices.
-
Utilize advanced threat protection features offered by Office365: Office365 offers a range of security features, including advanced threat protection and anti-phishing capabilities.
-
Monitor account activity for suspicious behavior: Regularly monitor account activity for unusual login attempts, email forwarding changes, or other suspicious actions.
-
Employ advanced security solutions like intrusion detection/prevention systems: These systems can detect and prevent malicious activity on your network.
-
Implement robust email security measures, including advanced threat protection and spam filtering: Advanced email security solutions can filter out malicious emails and prevent phishing attacks before they reach users' inboxes.
Conclusion
Office365 executive inbox hacking represents a significant and growing threat to businesses worldwide. The financial consequences can be catastrophic, impacting not only the bottom line but also the reputation and long-term viability of organizations. The vulnerability lies not just in technical weaknesses, but also in human error and a lack of robust security protocols. Implementing a multi-layered security approach is essential.
Key Takeaways: Protecting against Office365 executive inbox hacking requires a proactive and comprehensive strategy involving robust security measures, employee training, and vigilant monitoring. Neglecting these crucial steps exposes your organization to significant financial and reputational risk.
Call to Action: Don't let your organization become another victim of Office365 executive inbox hacking. Take proactive steps today to protect your valuable assets and secure your future. Invest in robust security solutions, train your employees, and stay vigilant against these increasingly sophisticated cyber threats. Learn more about protecting yourself from Office365 Executive Inbox Hacking by [link to relevant resource].

Featured Posts
-
 Millions Stolen Inside The Office365 Executive Inbox Hacking Scheme
Apr 27, 2025
Millions Stolen Inside The Office365 Executive Inbox Hacking Scheme
Apr 27, 2025 -
 Hair And Tattoo Transformations Lessons From Ariana Grandes Latest Look
Apr 27, 2025
Hair And Tattoo Transformations Lessons From Ariana Grandes Latest Look
Apr 27, 2025 -
 Understanding The Value Of Middle Managers In Modern Organizations
Apr 27, 2025
Understanding The Value Of Middle Managers In Modern Organizations
Apr 27, 2025 -
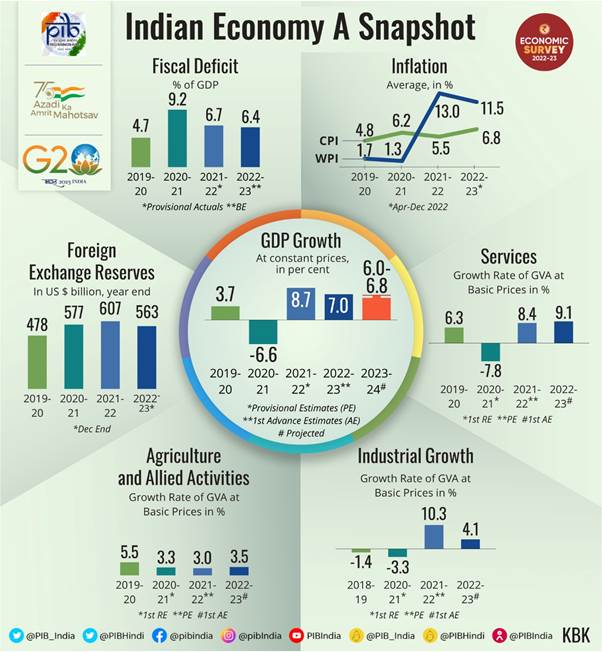 Canadian Travel Boycott A Fed Snapshot Of Economic Impact
Apr 27, 2025
Canadian Travel Boycott A Fed Snapshot Of Economic Impact
Apr 27, 2025 -
 Paolini Y Pegula Fuera Del Wta 1000 De Dubai
Apr 27, 2025
Paolini Y Pegula Fuera Del Wta 1000 De Dubai
Apr 27, 2025
