Office365 Security Breach: Millions In Losses From Executive Account Compromise
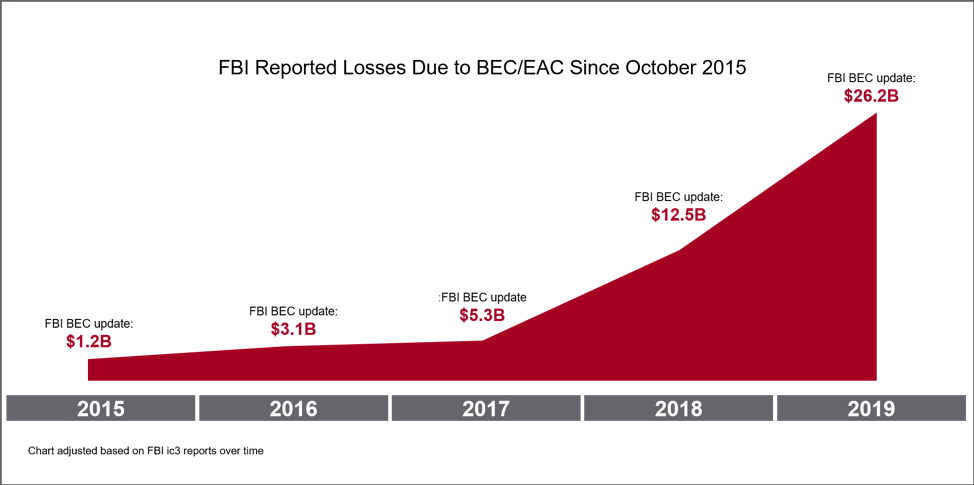
Table of Contents
Understanding the Vulnerabilities of Executive Office365 Accounts
Executive accounts are prime targets for cybercriminals due to their high-level access and authority. Understanding the vulnerabilities is the first step toward robust protection.
Phishing and Social Engineering Attacks
Phishing emails and sophisticated social engineering tactics are expertly crafted to exploit human psychology. These attacks often leverage CEO fraud, where attackers impersonate executives to trick employees into transferring funds or revealing sensitive information. Spear phishing, a highly targeted form of phishing, uses personalized information to increase its effectiveness. Executives, due to their decision-making power and access to sensitive financial information, are particularly vulnerable to executive email compromise.
- CEO Fraud: Attackers impersonate the CEO or other high-ranking executives to initiate fraudulent transactions.
- Spear Phishing: Highly targeted emails containing personalized information to bypass spam filters and appear legitimate.
- Whaling: A type of spear phishing specifically targeting high-profile individuals like CEOs and CFOs.
Weak or Reused Passwords
Weak passwords and password reuse across multiple platforms are major security risks. Credential stuffing attacks, where stolen credentials are tested against multiple accounts, are incredibly effective against accounts using weak or recycled passwords. This can easily compromise executive accounts, granting attackers access to sensitive company data and financial systems.
- Weak Passwords: Easy-to-guess passwords such as "password123" or variations of personal information.
- Password Reuse: Using the same password across multiple accounts, amplifying the impact of a single breach.
- Credential Stuffing: Automated attacks using lists of stolen usernames and passwords to gain access to accounts.
Lack of Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is crucial for enhancing Office365 security. Even if credentials are stolen, MFA adds an extra layer of security, preventing unauthorized access. Various MFA methods exist, including one-time codes, biometric authentication, and security keys, each offering varying levels of protection. Two-factor authentication (2FA) is a common form of MFA that requires two distinct authentication methods.
- One-Time Codes (OTP): Generated codes sent via text message or email.
- Biometric Authentication: Using fingerprints, facial recognition, or other biometric data.
- Security Keys: Physical devices that generate unique codes for authentication.
The Dire Financial Consequences of an Office365 Compromise
The financial ramifications of an Office365 security breach can be catastrophic. The consequences extend far beyond the immediate financial losses.
Direct Financial Losses
Compromised executive accounts can lead to significant financial fraud, including embezzlement and wire transfer fraud. Attackers can initiate unauthorized payments, transfer funds to offshore accounts, and manipulate financial records. The potential loss depends on company size and the scope of the breach.
- Wire Transfer Fraud: Unauthorized transfers of large sums of money to fraudulent accounts.
- Embezzlement: The theft or misappropriation of company funds by employees or insiders.
- Data Breach Costs: Expenses related to investigation, remediation, legal fees, and notification of affected parties.
Reputational Damage and Loss of Client Trust
A security breach severely damages a company's reputation and brand image. The loss of client trust can result in lost business, reduced investment, and long-term financial instability. This reputational damage can take years to overcome.
- Loss of Clients: Customers may switch to competitors due to concerns about data security.
- Decreased Investor Confidence: Investors may withdraw investments or hesitate to invest in the future.
- Negative Media Coverage: Negative publicity can severely impact a company's public image.
Legal and Regulatory Penalties
Data breaches can trigger significant legal liabilities and regulatory fines. Regulations like GDPR and CCPA impose strict requirements for data protection and breach notification. Non-compliance can result in substantial penalties and legal action.
- GDPR (General Data Protection Regulation): EU regulation concerning data protection and privacy.
- CCPA (California Consumer Privacy Act): California law providing consumers with rights regarding their personal data.
- Legal Liability: Lawsuits from affected individuals or businesses.
Best Practices for Preventing Office365 Executive Account Breaches
Implementing robust security measures is crucial to prevent Office365 executive account breaches. A multi-layered approach is essential.
Implementing Robust MFA
Multi-factor authentication (MFA) should be mandatory for all executive accounts. Consider using a combination of methods for enhanced security. Regularly review and update your MFA policies to adapt to evolving threats.
- Enforce MFA for all executive accounts.
- Use a variety of MFA methods (OTP, security keys, etc.).
- Regularly review and update MFA policies.
Security Awareness Training
Regular security awareness training is vital for all employees, particularly executives. Training should cover phishing recognition, social engineering tactics, and password security best practices. Phishing simulations can help employees identify and report suspicious emails.
- Conduct regular security awareness training for all employees.
- Include realistic phishing simulations in the training program.
- Emphasize password management and strong password creation techniques.
Advanced Threat Protection (ATP)
Advanced Threat Protection (ATP) solutions provide an additional layer of security within the Office365 environment. ATP detects and prevents malicious emails and attachments, reducing the risk of executive account compromise.
- Implement Microsoft Defender for Office 365 or a comparable ATP solution.
- Configure ATP to detect and block phishing emails and malicious attachments.
- Regularly review ATP logs and alerts.
Conclusion: Protecting Your Organization from Office365 Security Breaches
The financial consequences of an Office365 security breach targeting executive accounts can be devastating. By implementing robust MFA, comprehensive security awareness training, and advanced threat protection solutions, organizations can significantly reduce their risk. Don't wait until it's too late. Invest in robust Office365 security measures today to protect your organization from devastating financial losses and maintain your competitive edge. Proactive security is not an expense; it's an investment in your organization's future.

Featured Posts
-
 Gensol Promoters Face Pfc Action Over False Documents In Eo W Transfer
Apr 27, 2025
Gensol Promoters Face Pfc Action Over False Documents In Eo W Transfer
Apr 27, 2025 -
 Autism Research Controversy Anti Vaccination Advocate In Charge
Apr 27, 2025
Autism Research Controversy Anti Vaccination Advocate In Charge
Apr 27, 2025 -
 Premier Leagues Fifth Champions League Spot Near Certainty
Apr 27, 2025
Premier Leagues Fifth Champions League Spot Near Certainty
Apr 27, 2025 -
 Cybercriminal Made Millions Targeting Executive Office365 Accounts Fbi Investigation
Apr 27, 2025
Cybercriminal Made Millions Targeting Executive Office365 Accounts Fbi Investigation
Apr 27, 2025 -
 440 Million Turkish Logistics Company Acquired By Cma Cgm
Apr 27, 2025
440 Million Turkish Logistics Company Acquired By Cma Cgm
Apr 27, 2025
